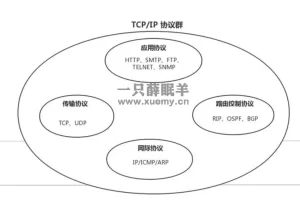
TCP/IP协议根底学问整理
TCP/IP
从字面意义上讲,有人可能会认为 TCP/IP 是指 TCP 和 IP 两种协议。实际生活当中有时也确实就是指这两种协议。然而在很多情况下,它只是利用 IP 进行通信时所必须用到的协议群的统称。具体来说,IP 或 ICMP、TCP 或 UDP、TELNET 或 FTP、以及 HTTP 等都属于 TCP/IP 协议。他们与 TCP 或 IP 的关系紧密,是互联网必不可少的组成部分。TCP/IP 一词泛指这些协议,因此,有时也称 TCP/IP 为网际协议群。
互联网进行通信时,需要相应的网络协议,TCP/IP 原本就是为使用互联网而开发制定的协议族。因此,互联网的协议就是 TCP/IP,TCP/IP 就是互联网的协议。
概括:TCP/IP是网际协议群
![图片[1]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/1-23.webp)
OSI七层模型
TCP/IP概念层模型
功能
TCP/IP协议族
应用层
应用层
文件传输,电子邮件,文件服务,虚拟终端
TFTP,HTTP,SNMP,FTP,SMTP,DNS,Telnet
表示层
数据格式化,代码转换,数据加密
没有协议
会话层
解除或建立与别的接点的联系
没有协议
传输层
传输层
提供端对端的接口
TCP,UDP
网络层
网络层
为数据包选择路由
IP,ICMP,RIP,OSFPF,BGP,IGMP
数据链路层
链路层
传输有地址的帧以及错误检测功能
SLIP,CSLIP,PPP,ARP,RARP,MTU
物理层
以二进制数据形式在物理媒体上传输数据
ISO02110,IEEE802,IEEE802.2 UDP和TCP的区别
UDP:USER DATAGRAM PROTOCOL
![图片[2]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/2.gif)
TCP:TRANSMISSION CONTROL PROTOCOL
![图片[3]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/3.gif)
| UDP | TCP | |
|---|---|---|
| 是否连接 | 无连接 | 面向连接 |
| 是否可靠 | 不可靠传输,不使用流量控制和拥塞控制 | 可靠传输,使用流量控制和拥塞控制 |
| 连接对象个数 | 支持一对一,一对多,多对一和多对多交互通信 | 只能是一对一通信 |
| 传输方式 | 面向报文 | 面向字节流 |
| 首部开销 | 首部开销小,仅8字节 | 首部最小20字节,最大60字节 |
| 适用场景 | 适用于实时应用(IP电话、视频会议、直播等) | 适用于要求可靠传输的应用,例如文件传输 |
三次握手
TCP Connection Establishment (Called, Three-Way Handshake)
The following events happens when a TCP connection is established:
- When a client initiate an active open by calling connect() function, then client TCP sends a “synchronize” (SYN), which includes client’s initial sequence number for the data which will be send on the connection.
- The TCP server acknowledges (ACK) the client’s SYN along with its own SYN containing the initial sequence number for the data that the server is going to send on the active connection.
- Finally, client TCP acknowledge the server’s SYN and connection will become active.
Three packets required to make an active connection, so that it is called three-way handshake.
![图片[4]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/4-16.webp)
为什么 TCP 建立连接需要三次握手,而不是两次?
1.为了防止出现失效的连接请求报文段被服务端接收的情况,从而产生错误。
2.如果只是两次握手,只有发起方序列号被确认,另一方序列号得不到确认,不能实现可靠数据传输
四次握手
TCP Connection Termination (May called, Four-Way Handshake)
The following events happens when a TCP connection is closed:
- When a TCP client/server close the connection first (active close), then TCP sends a FIN segment.
- On the other hand who receives the FIN performs the passive close and acknowledged by TCP.
- Later of time the application that received the end-of-file will close its socket and thus TCP to send a FIN.
- Finally, TCP which receives this final FIN (the end which initiated the active close) acknowledges the FIN.
Four packets required to close an active connection, so that it is called four-way handshake.
![图片[5]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/5-14.webp)
Socket编程实现TCP握手
基本思路:
返回:0-OK;-1-出错
出错报错提示 没出错正常进行下一步
![图片[6]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/6-12-1024x723.webp)
![图片[7]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/7-11-1024x650.webp)
常见的参数
AF_LOCAL:Unix 系统本地通信
AF_INET:IPV4
AF_INET6:IPV6
Server.c
#include
#include
#include
#include
#include
#include
#include
#include
#define PORT 1234
#define BACKLOG 1
#define MAXDATASIZE 100
int main( void )
{
int listenfd, connectfd, n, m;
struct sockaddr_in server; /*服务器端地址 */
struct sockaddr_in client; /* 客户端地址 */
socklen_t addrlen;
char buf[MAXDATASIZE];
if ( (listenfd = socket( AF_INET, SOCK_STREAM, 0 ) ) == -1 )
{
perror( "socket() error.\n" );
exit( 1 );
}
int opt = SO_REUSEADDR;
setsockopt( listenfd, SOL_SOCKET, SO_REUSEADDR, &opt, sizeof(opt) );//允许套接口和一个已在使用中得地址绑定。
bzero( &server, sizeof(server) );//置0
server.sin_family = AF_INET;
server.sin_port = htons( PORT );
server.sin_addr.s_addr = htonl( INADDR_ANY );
if ( bind( listenfd, (struct sockaddr *) &server, sizeof(struct sockaddr) )
== -1 )
{
perror( "bind() error.\n" );
exit( 1 );
}
if ( listen( listenfd, BACKLOG ) == -1 )
{
perror( "listen() error.\n" );
exit( 1 );
}
addrlen = sizeof(client);
while ( 1 )
{
if ( (connectfd = accept( listenfd, (struct sockaddr *) &client,&addrlen ) ) == -1 )
{
perror( "accept() error.\n" );
exit( 1 );
}
printf( "Your Local ip: %s, port: %d\n", inet_ntoa( client.sin_addr ), ntohs( client.sin_port ) );
send( connectfd, "Welcome to my server\n", 22, 0 );
/* 字符反转 */
while ( (n = read( connectfd, buf, MAXDATASIZE ) ) > 0 )
{
int m = strlen( buf );
char rever[m];
/* 反转过程:
比如我输入的是ruifosang
这里m=9
rever[8]=buf[0] g
rever[7]=buf[1] n
rever[6]=buf[2] a
rever[5]=buf[3] s
rever[4]=buf[4] o
rever[3]=buf[5] f
rever[2]=buf[6] i
rever[1]=buf[7] u
rever[0]=buf[8] r
*/
for ( int i = 0; i < m; i++ )
{
rever[m - i - 1] = buf[i];
}
rever[m] = '\0';
/* 接收客户端传来的字符串 */
printf( "Send reverse string:%s\n", buf );
/* 如果输入quit就退出 */
if ( strcmp( rever, "tiuq" ) == 0 )
{
exit( 1 );
}
write( connectfd, rever, n );
}
close( connectfd );
}
close( listenfd );
}Client.c
#include
#include
#include
#include
#include
#include
#include
#define PORT 1234
#define MAXDATASIZE 100
int main( int argc, char *argv[] )
{
int fd, numbytes, i;
char buf[MAXDATASIZE];
char sendStr[MAXDATASIZE], recStr[MAXDATASIZE];
struct hostent * he;
struct sockaddr_in server;
if ( argc != 2 )
{
printf( "Usage: %s \n", argv[0] );
exit( 1 );
}
if ( (he = gethostbyname( argv[1] ) ) == NULL )
{
perror( "gethostbyname() error.\n" );
exit( 1 );
}
if ( (fd = socket( AF_INET, SOCK_STREAM, 0 ) ) == -1 )
{
perror( "socket() error.\n" );
exit( 1 );
}
bzero( &server, sizeof(server) );
server.sin_family = AF_INET;
server.sin_port = htons( PORT );
server.sin_addr = *( (struct in_addr *) he->h_addr);
if ( i = connect( fd, (struct sockaddr *) &server, sizeof(server) ) == -1 )
{
perror( "connect() error\n." );
exit( 1 );
}
if ( (numbytes = recv( fd, buf, MAXDATASIZE, 0 ) ) == -1 )
{
perror( "recv() error.\n" );
exit( 1 );
}
buf[numbytes] = '\0';
printf( "%s", buf );
/* 在没有报错的情况下 */
while ( i != -1 )
{
printf( "Please input string: " );
/* 接收输入的字符串 */
scanf( "%s", &sendStr );
sendStr[strlen( sendStr )] = '\0';
/* 如果输入的字符串为quit则退出 */
if ( strcmp( sendStr, "quit" ) == 0 )
{
write( fd, sendStr, strlen( sendStr ) + 1 );
exit( 1 );
}
write( fd, sendStr, strlen( sendStr ) + 1 );
read( fd, recStr, MAXDATASIZE );
/* 打印反转字符串 */
printf( "Received reverse string:%s\n", recStr );
}
close( fd );
}连接成功后服务器端也会输出客户端的地址信息,并等待客户端发送信息从客户端输入字符串,并发送给服务器,服务器进行翻转后,发回客户端打印出来。
![图片[8]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/8-10-1024x574.webp)
HTTPS/HTTP
HTTPS: Secure Hypertext Transfer Protocol
HTTP: Hypertext Transfer Protocol
HTTPS 的出发点是解决HTTP明文传输时信息被篡改和监听的问题。
![图片[9]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/9-9-1024x404.webp)
- 为了兼顾性能和安全性,使用了非对称加密+对称加密的方案。
- 为了保证公钥传输中不被篡改,又使用了非对称加密的数字签名功能,借助CA机构和系统根证书的机制保证了HTTPS证书的公信力。
加解密流程流程
![图片[10]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/10-6-1024x706.webp)
- 用户在浏览器发起HTTPS请求,默认使用服务端的443端口进行连接;
- HTTPS需要使用一套CA数字证书,证书内会附带一个公钥Pub,而与之对应的私钥Private保留在服务端不公开;
- 服务端收到请求,返回配置好的包含公钥Pub的证书给客户端;
- 客户端收到证书,校验合法性,主要包括是否在有效期内、证书的域名与请求的域名是否匹配,上一级证书是否有效(递归判断,直到判断到系统内置或浏览器配置好的根证书),如果不通过,则显示HTTPS警告信息,如果通过则继续;
- 客户端生成一个用于对称加密的随机Key,并用证书内的公钥Pub进行加密,发送给服务端;
- 服务端收到随机Key的密文,使用与公钥Pub配对的私钥Private进行解密,得到客户端真正想发送的随机Key;
- 服务端使用客户端发送过来的随机Key对要传输的HTTP数据进行对称加密,将密文返回客户端;
- 客户端使用随机Key对称解密密文,得到HTTP数据明文;
- 后续HTTPS请求使用之前交换好的随机Key进行对称加解密。
http和https对比
| http | VS | https |
|---|---|---|
| 明文传输,网站或相关服务与用户之间的数据交互无加密,极易被监听,破解甚至篡改。 | 传输方式 | 在 HTTP 下加入了 SSL 层,是数据传输变成加密模式,从而保护了交换数据隐私和完整性,简单来说它就是安全版的 HTTP。 |
| 无任何身份认证,用户无法通过http辨认出网站的真实身份。 | 身份认证 | 经过CA多重认证,包括域名管理权限认证,单位身份合法性确认等。EV证书甚至可以直接在浏览器地址栏显示单位名称,提升用户体验。 |
| 无任何使用成本,所有网站默认即 http 模式。 | 实现成本 | 需要申请SSL证书来实现https,价格几百元到上万元不等 |
| 80端口 | 连接端口 | 443端口 |
提示网站不安全: 当您的网站上有类似注册登陆等表单时,用户一旦进行输入,Chrome浏览器便红色高亮显示“不安全”: 当您的网站上有类似注册登陆等表单时,用户一旦进行输入,Chrome浏览器便红色高亮显示“不安全”: | 浏览器兼容性 | 提示网站连接是安全的: 当您申请的是“EVSSL证书”时,浏览器地址栏会直接显示您的单位名称,可显著提升网站用户的信任度和单位形象: 当您申请的是“EVSSL证书”时,浏览器地址栏会直接显示您的单位名称,可显著提升网站用户的信任度和单位形象: |
| 对http网站无任何优待。 | SEO优化 | 百度谷歌等官方声明提高 https 网站的排名权重。 |
| 极易被黑客或者恶意的同行进行流量劫持等。 | 网站劫持 | 隐私信息加密,防止流量劫持 |
| 当网站需要与第三方平台进行对接时,通常不接受http这种连接。 | 数据对接 | 微信小程序,抖音,苹果等等越来越多的平台只接受https这种加密的安全链接。 |
| 经常因为没有https,而被各个浏览器或者其他平台显示风险警告,导致损害用户的信任度。 | 网站形象 | 为网站的用户营造安全的浏览环境,是网站的基本责任,也是赢得用户信赖的一个重要因素。 |
| 无任何风险保障,当网站数据传输被截取导致重大损失时,只有网站运营者自己承担。 | 风险保障 | 拥有10万-175万美元的商业保险,当网站数据传输被破解时,有巨额的保障额度。 |
通过F12开发者工具可以查看到网站使用的证书以及具体到期时间
![图片[11]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/15-2-1024x631.webp)
给服务器配置HTTPS
先申请证书,可以通过腾讯云签发免费的TRUSTASIA的证书,仅需要进行DNS校验或者文件校验即可。
校验成功后得到fullchain.pem和privkey.pem两个文件
要满足PCI DSS配置https时候需要注意的,使用HSTS:HTTP Strict Transport Security
nginx服务器为例,要加入
add_header Strict-Transport-Security "max-age=31536000";注:PCI DSS支付卡行业安全标准,Apple ATS规范
nginx.conf文件
server
{
listen 80;
listen 443 ssl http2;
server_name www.ruifosang.com;#域名
index index.php index.html index.htm default.php default.htm default.html;#首页文件
root /www/wwwroot/www.ruifosang.com;#网站目录
add_header Strict-Transport-Security "max-age=31536000";#使用HSTS
#HTTP_TO_HTTPS_START
if ($server_port !~ 443){
rewrite ^(/.*)$ https://$host$1 permanent;#将http内容全部跳转到https上
}
#HTTP_TO_HTTPS_END
ssl_certificate /www/wwwroot/cert/www.ruifosang.com/fullchain.pem;
ssl_certificate_key /www/wwwroot/cert/www.ruifosang.com/privkey.pem;
ssl_protocols TLSv1.1 TLSv1.2 TLSv1.3;#启用的TLS协议
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE;#加密套件
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
error_page 497 https://$host$request_uri;
#SSL-END
#ERROR-PAGE-START 错误页配置,可以注释、删除或修改
#error_page 404 /404.html;
#error_page 502 /502.html;
#ERROR-PAGE-END
#PHP-INFO-START PHP引用配置,可以注释或修改
include enable-php-71.conf;
#PHP-INFO-END
#REWRITE-START URL重写规则引用,修改后将导致面板设置的伪静态规则失效
include /www/server/panel/vhost/rewrite/www.ruifosang.com.conf;
#REWRITE-END
#禁止访问的文件或目录
location ~ ^/(\.user.ini|\.htaccess|\.git|\.svn|\.project|LICENSE|README.md)
{
return 404;
}
#一键申请SSL证书验证目录相关设置
location ~ \.well-known{
allow all;
}
location ~ .*\.(gif|jpg|jpeg|png|bmp|swf)$
{
expires 30d;
error_log off;
access_log /dev/null;
}
location ~ .*\.(js|css)?$
{
expires 12h;
error_log off;
access_log /dev/null;
}
access_log /www/wwwlogs/www.ruifosang.com.log;
error_log /www/wwwlogs/www.ruifosang.com.error.log;
}DNS
WHAT IS DNS?
The Domain Name System (DNS) is the phonebook of the Internet. Humans access information online through domain names. Web browsers interact through Internet Protocol (IP) addresses. DNS translates domain names to IP addresses so browsers can load Internet resources.
DNS域名系统,DNS 将域名转换为 IP 地址,以便浏览器能够加载 Internet 资源。
Each device connected to the Internet has a unique IP address which other machines use to find the device. DNS servers eliminate the need for humans to memorize IP addresses such as 192.168.1.1 (in IPv4), or more complex newer alphanumeric IP addresses such as 2400:cb00:2048:1::c629:d7a2 (in IPv6).
How does DNS work?
DNS解析过程:主机名→计算机友好的 IP 地址
The process of DNS resolution involves converting a hostname (such as www.example.com) into a computer-friendly IP address (such as 192.168.1.1). An IP address is given to each device on the Internet, and that address is necessary to find the appropriate Internet device – like a street address is used to find a particular home. When a user wants to load a webpage, a translation must occur between what a user types into their web browser (example.com) and the machine-friendly address necessary to locate the example.com webpage.
In order to understand the process behind the DNS resolution, it’s important to learn about the different hardware components a DNS query must pass between. For the web browser, the DNS lookup occurs “ behind the scenes” and requires no interaction from the user’s computer apart from the initial request.
There are 4 DNS servers involved in loading a webpage:
- DNS解析器 (DNS recursor) – The recursor can be thought of as a librarian who is asked to go find a particular book somewhere in a library. The DNS recursor is a server designed to receive queries from client machines through applications such as web browsers. Typically the recursor is then responsible for making additional requests in order to satisfy the client’s DNS query.
- 根域名服务器 (Root nameserver) – The root server is the first step in translating (resolving) human readable host names into IP addresses. It can be thought of like an index in a library that points to different racks of books – typically it serves as a reference to other more specific locations.
- TLD 域名服务器 (TLD nameserver) – The top level domain server (TLD) can be thought of as a specific rack of books in a library. This nameserver is the next step in the search for a specific IP address, and it hosts the last portion of a hostname (In example.com, the TLD server is “com”).
- 权威性域名服务器(Authoritative nameserver) – This final nameserver can be thought of as a dictionary on a rack of books, in which a specific name can be translated into its definition. The authoritative nameserver is the last stop in the nameserver query. If the authoritative name server has access to the requested record, it will return the IP address for the requested hostname back to the DNS Recursor (the librarian) that made the initial request.
What is IPv6?
IPv6 is the next generation Internet Protocol (IP) address standard intended to supplement and eventually replace IPv4, the protocol many Internet services still use today. Every computer, mobile phone, home automation component, IoT sensor and any other device connected to the Internet needs a numerical IP address to communicate between other devices. The original IP address scheme, called IPv4, is running out of addresses due to its widespread usage from the proliferation of so many connected devices.
What is IPv4?
IPv4 stands for Internet Protocol version 4. It is the underlying technology that makes it possible for us to connect our devices to the web. Whenever a device accesses the Internet, it is assigned a unique, numerical IP address such as 99.48.227.227. To send data from one computer to another through the web, a data packet must be transferred across the network containing the IP addresses of both devices.
Why Support IPv6? What are the benefits of IPv6?
IPv6 (Internet Protocol version 6) is the sixth revision to the Internet Protocol and the successor to IPv4. It functions similarly to IPv4 in that it provides the unique IP addresses necessary for Internet-enabled devices to communicate. However, it does have one significant difference: it utilizes a 128-bit IP address.
Key benefits to IPv6 include:
- No more NAT (Network Address Translation)
- Auto-configuration
- No more private address collisions
- Better multicast routing
- Simpler header format
- Simplified, more efficient routing
- True quality of service (QoS), also called “flow labeling”
- Built-in authentication and privacy support
- Flexible options and extensions
- Easier administration (no more DHCP)
IPv4 uses a 32-bit address for its Internet addresses. That means it can provide support for 2^32
IP addresses in total around 4.29 billion. That may seem like a lot, but all 4.29 billion IP addresses have now been assigned, leading to the address shortage issues we face today.
IPv6 utilizes 128-bit Internet addresses. Therefore, it can support 2^128 Internet addresses—340,282,366,920,938,463,463,374,607,431,768,211,456 of them to be exact. The number of IPv6 addresses is 1028 times larger than the number of IPv4 addresses. So there are more than enough IPv6 addresses to allow for Internet devices to expand for a very long time.
The text form of the IPv6 address is xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx, where each x is a hexadecimal digit, representing 4 bits. Leading zeros can be omitted. The double colon (::) can be used once in the text form of an address, to designate any number of 0 bits.
With Dual-IP stacks, your computers, routers, switches, and other devices run both protocols, but IPv6 is the preferred protocol. A typical procedure for businesses is to start by enabling both TCP/IP protocol stacks on the wide area network (WAN) core routers, then perimeter routers and firewalls, followed by data-center routers and finally the desktop access routers.
概况:
IPV4面临着资源短缺的问题,而IPV6可以分配更多的地址,并且他有着以下优势:
- 不再有NAT(网络地址转换)
- 自动配置
- 不再有私人地址冲突
- 更好的组播路由
- 标头格式更简单
- 简化,更高效的路由
- 真正的服务质量(QoS),也称为“流标签”
- 内置身份验证和隐私支持
- 灵活的选项和扩展
- 简化管理(不再需要DHCP)
ARP
ARP: Address Resolution Protocol
ARP 是一种解决地址问题的协议。以目标 IP 地址为线索,用来定位下一个应该接收数据分包的网络设备对应的 MAC 地址。不过 ARP 只适用于 IPv4,不能用于 IPv6。IPv6 中可以用 ICMPv6 替代 ARP 发送邻居探索消息。
RARP 是将 ARP 反过来,从 MAC 地址定位 IP 地址的一种协议。
ARP欺骗
正常情况下的ARP请求与应答:
![图片[12]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/16-2-1024x397.webp)
PC2广播ARP请求,询问IP地址为192.168.3.2的主机的MAC地址。 PC1收到广播帧,发出ARP应答,告诉PC2自己是192.168.3.2,MAC地址是aa:aa:aa:aa:aa:aa。
单向ARP欺骗
![图片[13]-TCP/IP协议根底学问整理-一只薛眠羊](https://www.xuemy.cn/wp-content/uploads/2023/02/17-2-1024x660.webp)
PC1广播ARP请求,询问IP地址为192.168.3.1的主机的MAC地址。 PC3收到广播
帧,发出ARP应答,告诉PC1自己是192.168.3.1,MAC地址是cc:cc:cc:cc:cc:cc。(这之后,PC1发给PC2的所有流量都会发给PC3)
双向ARP欺骗
跟上面图类似,PC3同时接收PC1、PC2的流量(本来PC1发给PC2,PC2发给PC1的流量)
可以使用arpspoof工具进行欺骗,kali里面就有(待验证)
ICMP
ICMP: Internet Control Message Protocol
ICMP 的主要功能包括,确认 IP 包是否成功送达目标地址,通知在发送过程当中 IP 包被废弃的具体原因,改善网络设置等。IPv4 中 ICMP 仅作为一个辅助作用支持 IPv4。也就是说,在 IPv4 时期,即使没有 ICMP,仍然可以实现 IP 通信。然而,在 IPv6 中,ICMP 的作用被扩大,如果没有 ICMPv6,IPv6 就无法进行正常通信。












暂无评论内容